meta data for this page
Working with shadows
A shadow is a physical copy of the database file. When you need more than the typical level of security, it is possible to add a second hard disk on your machine and make a shadow copy of your database. When you have all data on one computer and it breaks down, you need rapid access to the data. Therefore you should typically create a shadow file on an external USB hard disk. Simply specify on this hard disk:
create shadow 1 'C:\db1.shd' (Full syntax and parameters can be found in the IBExpert documentation chapter, Creating a shadow.)
It is possible to create a shadow during runtime. You don't just have to create one shadow, you can create ten if you like, although it is not necessarily a good idea because each writing process must then be done eleven times and not just two!
After committing, the whole database file is copied to the shadow. This is also the fastest way to create a simple database copy on a USB disk as fast as possible, as an alternative to a a backup and restore which takes some time, especially the restore, because in the restore process, the indices are rewritten. You then simply need to use GFIX to activate it to turn it into an active database when needed. The CREATE SHADOW command makes a physical copy of the database pages from the original file to the shadow file, without thinking about what is written inside.
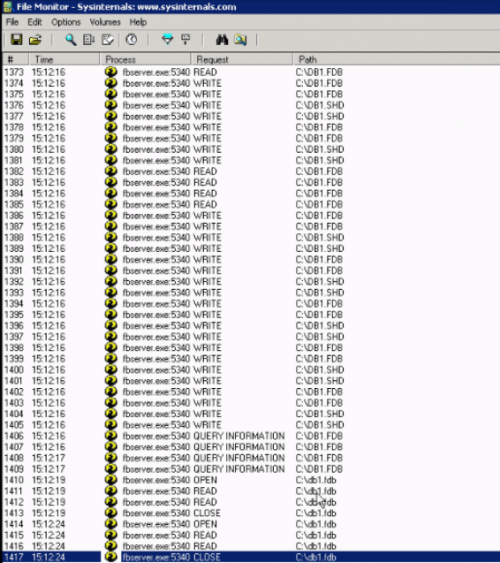
When viewing a file monitor filtered for operations on the db1 database, there are a number of operations on both the database file (.fdb) and the shadow file (.shd):
In a production environment, when a select is performed for example, all the read statements are done on the fdb file, the shadow file is only used for writing. In spite of this it is still recommend you use a very fast external hard drive for an active shadow, as you may notice a drop in performance with the double amount of write operations now being made to both databases.
If you encounter the problem that the shadow file is now the only file that you have, because your main computer has broken down, to turn the shadow file into a valid database, you need to use the Firebird/InterBase® tool, gfix.
On the command line type:
C:\> gfix localhost/3021:C:\db1.shd –activate
and that's all you need to enter to get a valid database!
So for example, you need a copy of your main database which is 5 GB large; you just create a shadow on a USB hard disk, commit the shadow, and after everything is committed, pull it out. Forced Writes handles both databases in the same way. When something is written in the TIP, it is written in both files. When it is written on a page at the end of the file, it is written at the end of both files. So you always have the possibility to make a high speed backup of your database, and you can activate this backup with a simple batch command to turn it into a valid database.
In a shadow you have the same problems as in your main database. For example, when you have deleted all the records in your main database and you have already committed it, you will have the same problem in your shadow, because it is a physical copy of your main database file, nothing else.
So if you need an “undo” of your transactions, you need another concept, for example, a transaction log.
If the shadow is no longer available, the main database ignores the shadow (default setting). This is, for example, the reason why you can put a shadow on the USB hard disk, and directly remove it. The database server with the typical settings does not need to stop its work when the shadow is no longer available. In order to reactivate the shadow you will need to specify the CREATE SHADOW command again. For security reasons it is possible to specify that no new transactions can be started when the shadow is no longer available. However this option is seldom used, because the moment one of the hard disks stops working, no one can work at all. These options can be specified in the CREATE SHADOW statement.
Full details, along with the advantages and disadvantages of database shadow files, can be referred to in the IBExpert documentation chapter, Database Shadow Files.